A Request by United States Marine Field McConnell
for
Images Leading To A Proof by Contradiction Of Assertions Below
Plum City Online - (AbelDanger.net)
October 6, 2015
1. AD ASSERTS THAT SERCO – FOUNDED AS RCA GB 1929 – HAS BEEN DEPLOYING 'RIOT CLUB' ASSASSINS under the direction of Bullingdon Club alumni to extort state leaders into reducing carbon footprints by killing citizens.
2. AD ASSERTS THAT SERCO'S HSBC BANKER ORDERED FBI DIRECTOR JAMES COMEY TO WIPE TIMELINES OFF CARLY FIORINA'S HP SERVERS on the Navy/Marine Corps Intranet (NMCI) and thereby destroy any evidence of synchronicity between Riot Club betting since 9/11 and Bitcoin death-pool frauds.
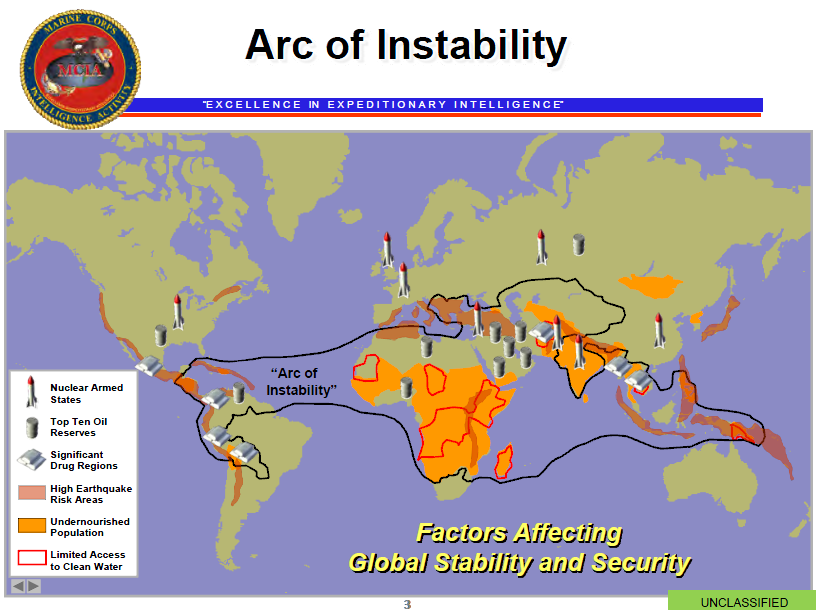
3. AD ASSERTS SERCO USES 8(A) DIGITAL FIRES IN A MARINE CORPS (MC) ARC OF INSTABILITY TO CAMOUFLAGE A SYRIAN GENOCIDE where the carbon footprints of thousands of 'useless breathers' are being wiped by their 'more-equal' leaders from the Riot Club's Animal Farm.
United States Marine Field McConnell (http://www.abeldanger.net/2010/01/field-mcconnell-bio.html) is writing an e-book "Shaking Hands With the Devil's Clocks" and invites readers to e-mail him images (examples below) for a proof by contradiction of the three assertions above.
Run by Serco (formerly RCA GB 1929) since 1988
Riot Club Assassins WWII
Run by Serco since 1994
Run by Serco since 1994
Run by Serco since 1994
Run by Serco since 1953
The Mayfair Set episode 1- Who Pays Wins
"The Riot Club is a 2014 British drama thriller film directed by Lone Scherfig and written by Laura Wade, based on Wade's 2010 play Posh.[1] The film stars Max Irons, Sam Claflin and Douglas Booth.[2] It is set among the Riot Club, a fictional all-male, exclusive dining club at Oxford University. When the play Poshpremiered, the Riot Club was often described as a thinly veiled version of the real-life Bullingdon Club, or High Trees Society although according to Wade it is entirely fictitious.[3]"
"Obama's "Fake War" against the Islamic State (ISIS). The Islamic State is Protected by the US and its Allies
By Prof Michel Chossudovsky
Global Research, August 23, 2015
Global Research 23 February 2015
Region: Middle East & North AfricaTheme: 9/11 & 'War on Terrorism', Media Disinformation, US NATO War Agenda In-depth
Report: IRAQ REPORT, SYRIA: NATO'S NEXT WAR?
One Year since the outset of the US bombing campaign "against ISIS" in Syria and Iraq. August 8, 2014 marked the onset of the bombing campaign.
This article was first published in February 2015.
UPDATE (August 22, 2015)
According to figures released by U.S. Central Command (CENTCOM), "the U.S. and its coalition partners have struck 10,684 targets including 3,262 [so-called] ISIS buildings, 119 commandeered tanks, 1,202 vehicles and 2,577 fighting positions." The term "ISIS buildings" is a fake concept. Those buildings (including residential areas) are part of the civilian infrastructure of Iraq and Syria. The number of targets struck suggests an intense carpet bombing campaign geared towards the destruction of both Iraq and Syria. Official figures confirm that over a period of one year (August 8, 2014 to July 31, 2015) approximately "20,000 airstrikes — close air support, escort, and interdiction — have been launched; about 5,200 of those involved the release of at least one weapon." The cost of Operation Enduring Freedom, which has resulted in countless civilian deaths is officially of the order of 3.5 billion dollars. The overall budget of the DoD is of the order of 650 billion dollars.
Meanwhile, the ISIS which is construct of US intelligence, trained and financed by the US and its allies (including Saudi Arabia, Turkey) has not been defeated. On the contrary it has extended its grip throughout the Middle East.
The bombing raids in Syria, Iraq and more recently Yemen have not been the object of protests by the anti-war movement, nor has been considered a criminal undertaking under international law . The bombing raids have been portrayed by the media as part of a counterterrorism operation. The “Global War on Terrorism” has been accepted as a humanitarian undertaking.
Since August 2014, the US Air Force with the support of a coalition of 19 countries has relentlessly waged an intensified air campaign against Syria and Iraq allegedly targeting the Islamic State brigades.
According to Defense News, over 16,000 airstrikes were carried out from August 2014 to mid January 2015. Sixty percent of the air strikes were conducted by the US Air Force using advanced jet fighter and bombing capabilities (Aaron Mehta, "A-10 Performing 11 Percent of Anti-ISIS Sorties." Defense News, January 19, 2015.)
The airstrikes have been casually described by the media as part of a “soft” counter-terrorism operation, rather than an act of all out war directed against Syria and Iraq.
F-16 Fighting Falcon
This large scale air campaign which has resulted in countless civilian casualties has been routinely misreported by the mainstream media. According to Max Boot, senior fellow in national security at the Council on Foreign Relations. ”Obama’s strategy in Syria and Iraq is not working… [ because] the U.S. bombing campaign against ISIS has been remarkably restrained”. (Newsweek, February 17, 2015, emphasis added). Americans are led to believe that the Islamic State constitutes a formidable force confronting the US military and threatening Western Civilization. The thrust of media reporting is that the US Air Force has failed and that "Obama should get his act together" in effectively confronting this "Outside Enemy" of America.
According to CFR Max Boot, military escalation is the answer: what is required is for the president "to dispatch more aircraft, military advisers, and special operations forces, while loosening the restrictions under which they operate." (Ibid)
What kind of aircraft are involved in the air campaign? The F-16 Fighting Falcon,(above right), The F-15E Strike Eagle (image below), The A-10 Warthog, not to mention Lockheed Martin's F-22 Raptor stealth tactical fighter aircraft.
Question for Our Readers Why has the US Air Force not been able to wipe out the Islamic State which at the outset was largely equipped with conventional small arms not to mention state of the art Toyota pickup trucks?
From the very outset, this air campaign has NOT been directed against ISIS. The evidence confirms that the Islamic State is not the target. Quite the opposite.
The air raids are intended to destroy the economic infrastructure of Iraq and Syria.
The USAF-15E Strike Eagle
We call on our readers to carefully reflect on the following image, which describes the Islamic State convoy of pickup trucks entering Iraq and crossing a 200 km span of open desert which separates the two countries.
This convoy entered Iraq in June 2014.
What would have been required from a military standpoint to wipe out an ISIS convoy with no effective anti-aircraft capabilities? Without an understanding of military issues, common sense prevails.
If they had wanted to eliminate the Islamic State brigades, they could have "carpet" bombed their convoys of Toyota pickup trucks when they crossed the desert from Syria into Iraq in June.
The answer is pretty obvious, yet not a single mainstream media has acknowledged it.
The Syro-Arabian Desert is open territory (see map right). With state of the art jet fighter aircraft (F15, F22 Raptor, F16) it would have been –from a military standpoint– "a piece of cake," a rapid and expedient surgical operation, which would have decimated the Islamic State convoys in a matter of hours.
Instead what we have witnessed is an ongoing drawn out six months of relentless air raids and bombings, and the terrorist enemy is apparently still intact.
(In comparison, the NATO bombing raids of Yugoslavia in 1999 lasted about three months (March 24-June 10, 1999).
And we are led to believe that the Islamic State cannot be defeated by a powerful US led military coalition of 19 countries. The air campaign was not intended to decimate the Islamic State.
The counter-terrorism mandate is a fiction. America is the Number One “State Sponsor of Terrorism."
The Islamic State is not only protected by the US and its allies, it is trained and financed by US-NATO, with the support of Israel and Washington's Persian Gulf allies."
"Source: Comey confirms FBI team looking for breach of Clinton server, working '24/7'
By Catherine Herridge
Published September 30, 2015
FoxNews.com
Next batch of released Clinton emails will focus on Libya FBI Director James Comey has started briefing select lawmakers on the status of the investigation into Hillary Clinton's private server, and confirmed investigators are actively looking for evidence the server was compromised by a foreign entity or hacker, a congressional source told Fox News.
According to the source, Comey also reassured lawmakers his "top people" are handling the investigation. Comey said no resource is being spared and his team is working "24/7" to determine whether classified information was compromised, the source said.
No evidence of a breach has been confirmed so far, Fox News is told. The discussion was part of an intelligence briefing.
Speaking to an annual intelligence conference in September, Comey was asked by Fox News whether he could assure the public that the high-stakes investigation would not be influenced by politics.
"I'm not going to comment, as we never do, on any particular investigation of ours," Comey explained. "But I can assure the American people about this, I hope they already know it about the FBI, we are three things -- we're competent, we're independent, and we're honest. We do all of our work that way. We don't give a rip about politics. We follow the facts where they lead us. We do our work professionally, and we also do it in secret so that we don't jeopardize our ability to do it well."
Security analysts and lawmakers previously have cited the risk of any top-level official using a private email account. Asked about Clinton's email practices in a recent congressional hearing, National Security Agency Director Michael Rogers noted the use of a private email account by the foreign minister of Iran and Russia would present an "opportunity" for any spy agency.
As investigators continue their work, forensic computer specialists say any compromise of Clinton's account would leave malicious code on the server that can be recovered.
And an intelligence source close to the investigation recently told Fox News that the FBI maintains "the highest degree of confidence" emails are being recovered, adding that "shadows and ghosts" were on the server after messages were deleted.
Asked if the investigation would conclude before the end of the year, the congressional source said Comey said he "shared the sense of urgency," indicating the goal was to conclude before the full swing of the election cycle.
Fox News was told Comey emphasized his term as director is a fixed term of 10 years, implying he has the independence to pursue the investigation as any other.
The FBI has declined to comment, citing an ongoing investigation.
Fox News' Matthew Dean contributed to this report.
Catherine Herridge is an award-winning Chief Intelligence correspondent for FOX News Channel (FNC) based in Washington, D.C. She covers intelligence, the Justice Department and the Department of Homeland Security. Herridge joined FNC in 1996 as a London-based correspondent."
"Carly Fiorina May Have Server Issues Too
22Sep, 2015
by Dave Blount
Remember 2012, when the most vulnerable issue for Democrats was the overwhelmingly unpopular imposition of ObamaCare? The Establishment stuck Republicans with Mitt Romney, who couldn't use the issue because he was responsible for imposing ObamaCare's prototype on Massachusetts.
Since it looks like Obama will keep Shrillary out of jail, she remains the Democrat frontrunner for 2016. Her most vulnerable point is her illegal use of a private email server for top secret communications, presumably to cover her influence peddling activities. When the server was subpoenaed by Congress, she tried to wipe it — an arrogant crime that would land you or me in federal prison for some time.
Now the Establishment is using the media to hype Carly Fiorina. Here is what she says about Shrillary's server issues:
Fiorina said that it's "absolutely crystal clear" that Clinton broke the rules and that she's trying cover it up.
She pointed out that Clinton had a "server in her basement" for years, then decided to "wipe it clean" two years after leaving the State Department and before her presidential run.
But it is alleged that Fiorina has server issues too:
My name is Charles Nielsen and I was an employee with HP from 1/2000 until 8/2001. I worked in the Boise, Idaho Data Center. I was the sole Customer Engineer allowed to work on Carly’s Private Server. It was kept under lock and key and I was the only engineer allowed to work on it under the direct supervision of the Data Center Manager; I was new to the company and was used as a dupe. In March of 2001, just before Carly Fiorina had taken control of HP from Walter Hewlett, I was asked to remove the 5 hard drives from her personal server and physically destroy them with a hammer. I asked why I would destroy hard drives that at the time were worth over $15k apiece and I was told because she said so. Shortly after destroying all evidence of her conspiracy to take over the company she removed Walter Hewlett from the board of directors and made off with approximately $500 million dollars from the company with the rest of the board of directors ($100 million for Carly personally). All of her emails and all working documents were destroyed. I have kept my silence until now when I find it highly offensive that after laying off close to 30k workers and sending stock prices into the gutter ( $55 a share when Fiorina took over to a little less than $20 a share under her leadership) she is pretending she would never behave like Hillary has. Carly Fiorina is as corrupt as they come.
It would be nice for the mainstream media to use its resources to vet this guy so we know how seriously to take his allegations. But as we learned from the rise of Obama, vetting is not something the media does anymore. It digs up dirt on people it wants to destroy, and covers for those it wants to advance.
Right now it wants to advance Fiorino, I mean Fiorina — and not because she can win. Her record in both the business and political worlds consists of one failure precariously balanced atop another. In a general election the whole mess would collapse. That's not a bug; it's a feature.
Rush Limbaugh explains why the media has been hyping Fiorina and hiding her record:
"Because they want to get rid of Trump," Limbaugh said. …
"Look, this is very, very important for everybody to understand. And the reason it's very, very important is this is how they choose our nominees for us. …
"[I]t's not that they love Carly Fiorina. They love what supporting her now might enable them to accomplish, and that is get rid of a Republican who can win."
Romney could have beaten Obama in 2008. But mysteriously he was surpassed that year by the worst candidate the GOP could come up with, a sellout universally hated by the conservative base, John McCain.
Like the designated loser McCain, Fiorina is a tool the media will discard when she has served her usefulness.
On tips from Steve A and Wiggins. Hat tip: Liberty News. Cross-posted at Moonbattery."
"Defense Ammunition Center (DAC)
Contract Type
Fixed Price
Period of Performance 10/1/2008 to 9/30/2013
Project Overview:
Since 2008, Serco has assisted DAC with the analysis, design, development, implementation, management/ administration, and evaluation of integrated, enterprise-wide and component-specific training, learning, knowledge management, and strategic human resource management interventions that are critical to achieving their mission. Serco holds an OPM TMA TO with DAC and also a contract through GSA Millenia Lite. When the GSA contract could not support all of DACs needs, Serco recommended the use of the OPM TMA vehicle. Through these contracts, Serco provides training program management support to deliver multi-faceted best practice solutions in training development and delivery, knowledge management, portal technologies, course conversions (ILT and CBT to WBT), mobile performance applications, and Learning Management Systems support. Serco applies the ADDIE model to all course development activities including ILT, WBT, and leading-edge technologies including mobile performance applications. Serco provided LMS support and also developed and continues to manage DAC's Ammunition Community of Excellence."
"Defence Serco supports the armed forces of a number of countries around the world, including the United Kingdom, United States and Australia, working across land, sea, air, nuclear and space environments. Our mission is to deliver affordable defence capability and support to the armed forces. We work in partnership with our customers in government and the private sector to address the cost of defence, both financial and social, delivering affordable change and assured operational support services.
Click here to view a summary of Serco's defence solutions
In the UK and Europe:
Serco manages the UK Atomic Weapons Establishment (AWE) as part of a consortium with Lockheed Martin and Jacobs. AWE is one of the most advanced research, design and production facilities in the world, developing the sophisticated materials, quantum physics and computer modelling vital to the safe and effective maintenance of the UK's nuclear deterrent. AWE experts also play a leading role in nuclear non-proliferation and international nuclear security.
We enable the Royal Navy to move in and out of port at HM Naval Bases Faslane, Portsmouth and Devonport for operational deployment and training exercises. Managing a fleet of over 100 vessels, we operate tugs and pilot boats, provide stores, liquid and munitions transportation and provide passenger transfer services to and from ships for officers and crew.
We provide facilities and information systems support to the MoD's Defence Science and Technology Laboratory (Dstl), the UK government's leading defence research establishment, including a £400m programme to rationalise the Dstl estate. We also provide facilities management services to the Defence Estates in support of the UK military presence in Gibraltar.
Serco provides extensive engineering and maintenance support to UK military aviation, including to the Fleet Air Arm and Royal Air Force, working on over 16 military aircraft types, in addition to the logistical support services at RAF bases across the country, including Brize Norton, Lyneham and High Wycombe, the Headquarters of Air Command.
Our space and security specialists provide spacecraft operation and in-theatre support to the Skynet 5 secure military satellite communications network; we maintain the UK's anti-ballistic missile warning system at RAF Fylingdales and support the UK Air Surveillance and Control System (ASACS); Serco also supports the intelligence mission of the MoD and US Department of Defence at RAF Menwith Hill.
Serco enables the training of national security personnel through its services at the Defence Academy of the United Kingdom, the MoD's world class institute responsible for educating the military leaders of tomorrow; we train all of the RAF's helicopter pilots at the advanced training facility at RAF Benson; and we manage the Cabinet Office's Emergency Planning College, the government's training centre for crisis management and emergency planning.
In the UK, we also developed an approach that combines the introduction of windfarm friendly radar technology at RRH Trimingham, Staxton Wold and Brizlee Wood that has enabled >5GW windfarm development projects, which are equally important to the Department of Energy and Climate Change to meet its commitments to reduce greenhouse gas emissions and the Ministry of Defence"
"Digital Fires Instructor Serco - Camp Pendleton, CA Posted 377 days ago
Uses information derived from all military disciplines (e.g., aviation, ground combat, command and control, combat service support, intelligence, and opposing forces) to determine changes in enemy capabilities, vulnerabilities, and probable courses of action.
•Works directly with customers and team members to determine project scope and specifications.
•Provides research and analysis to support military organizations.
•May support development and analysis of products, including training modules, evaluation tools, etc.
•Presents analysis or products to customers.
•May support policy and procedure development for agency, interagency, or community-wide support.
•May interact with outside customers and functional peer groups.
• Participates in the development, testing, maintenance and delivery of training and educational programs and related materials in support of complex products and/or procedures.
• Knowledge on the operational employment and TTPs of the following C2 systems and software applications in the COC operating environment is required:, AFATDS, FBCB2-BFT, JADOCS, and supporting C2 systems/software applications found available for use the regimental/battalion Combat Operations Center (COC).
• Conducts training sessions and assists in evaluating the effectiveness of training activities.
• May assist with updating course documentation on a continuous basis to ensure timeliness and relevance.
• May work with engineering, technical support and manufacturing to ensure that course material reflects current product features. Desired Skills and Experience
•Requires a bachelor's degree in a related field; graduate degree preferred, plus 3 years' experience as a Military Analyst and/or formal military training. Appropriate clearance level required.
•Work is usually performed at a government site, some of which may be remote.
•Working conditions may vary.
•Travel may be required.
• Have attended DoD formal instructor courses, such as the Marine Corps' Formal School's Instructor's Course, or service equivalent
• Four years of documented experience instructing and employing their respective C2 system in support of MAGTF operations
• Background as an 0844 or 0848 MOS (USMC MOS, or equivalent USA MOS appropriate), with formal training and experience utilizing AFATDS (Advanced Field Artillery Target Data System), EMT (Effects Management Tool), PSS-SOF (Precision Strike Suite – Special Ops Forces)
• Active Secret Clearance or the ability to obtain a Secret clearance is required.
• Formal AFATDS Training required, Strike-Link, PSS-SOF, JADOCS experience desirable"
"Loan Improvement
Jan 31, 2001
SBA modernizes to help feed its growing programs
BY PATRICIA DAUKANTAS | GCN STAFF
Under a five-year plan for overhauling its information technology systems, the Small Business Administration recently acquired new software for financial and other administrative tasks.
By the time SBA celebrates its 50th anniversary in 2003, agency officials want all their programs up and running around the clock, chief financial officer Joseph Loddo said.
In the first phase of the modernization, the agency has upgraded systems for managing its extensive portfolio of guaranteed loans, chief operating officer Kristine Marcy said.
SBA processed its first electronic loan last November through its Sacramento, Calif., office and plans to add more private lenders during fiscal 2001. The agency's staffing level has dropped 22 percent over the past eight years, which is another reason to improve IT, Marcy said. Over the past decade, SBA's portfolio of loans to small and disadvantaged businesses has more than doubled to $50 billion.
'We're a small agency with a huge portfolio,' Marcy said. SBA supplies more than half of the U.S. venture capital available each year.
Seventy percent to 80 percent of the loans are booked through a preferred lender program, which involves nearly 7,000 banks, Marcy said. SBA guarantees the loans, just as the government backs student and housing loans.
'The financial and IT businesses were changing so rapidly, we had to make some changes to stay current with the private sector,' Marcy said. Banks had been asking SBA to make faster decisions on loan guarantees. The agency decided to aim for a turnaround time of one hour. In the second phase of modernization, SBA is revamping its financial, human resources, procurement and travel systems with Web-enabled Oracle Corp. applications.
Online in October
The financial system will use Oracle's U.S. Federal Financials 3.3, which meets the requirements of the Joint Financial Management Improvement Program.
SBA announced the $1.5 million Oracle contract late last year and plans to bring the software online by Oct. 1, Loddo said.
'We need to make sure we are appropriately sensitive to small businesses' and have small-business partners, not just Oracle, Marcy said.
The second-phase integrator, SRA International Inc. of Arlington, Va., has subcontracted with a number of small firms for things such as training and data conversion.
Also, a core team of senior SBA employees has been transferred away from day-to-day tasks to help with the modernization, Loddo said.
In the final phase of the modernization, SBA will upgrade the computers in its 8(a) Business Development Program, which assists small businesses in competing for government contracts, Marcy said. The agency wants to be able to improve its tracking of clients' successes and failures."
"8(a) Business Development Program[edit]
The 8(a) Business Development Program assists in the development of small businesses owned and operated by individuals who are socially and economically disadvantaged, such as women and minorities. The following ethnic groups are classified as eligible: Black Americans; Hispanic Americans; Native Americans (American Indians, Eskimos, Aleuts, or Native Hawaiians); Asian Pacific Americans (persons with origins from Burma, Thailand, Malaysia, Indonesia, Singapore, Brunei, Japan, China (including Hong Kong), Taiwan, Laos, Cambodia (Kampuchea), Vietnam, Korea, The Philippines, U.S. Trust Territory of the Pacific Islands (Republic of Palau), Republic of the Marshall Islands, Federated States of Micronesia, the Commonwealth of the Northern Mariana Islands, Guam, Samoa, Macao, Fiji, Tonga, Kiribati, Tuvalu, or Nauru); Subcontinent Asian Americans (persons with origins from India, Pakistan, Bangladesh, Sri Lanka, Bhutan, the Maldives Islands or Nepal). In 2011, the SBA, along with the FBI and the IRS, uncovered a massive scheme to defraud this program. Civilian employees of the U.S. Army Corps of Engineers, working in concert with an employee of Alaska Native Corporation Eyak Technology LLC allegedly submitted fraudulent bills to the program, totaling over 20 million dollars, and kept the money for their own use.[26] It also alleged that the group planned to steer a further 780 million dollars towards their favored contractor.[27]"
Yours sincerely,
Field McConnell, United States Naval Academy, 1971; Forensic Economist; 30 year airline and 22 year military pilot; 23,000 hours of safety; Tel: 715 307 8222
David Hawkins Tel: 604 542-0891 Forensic Economist; former leader of oil-well blow-out teams; now sponsors Grand Juries in CSI Crime and Safety Investigation

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.