Brief From United States Marine Field McConnell
Plum City Online - (AbelDanger.net)
July 27, 2015
1. In May 1998, United States Marine Field McConnell’s sister Kristine Marcy allegedly forced Aida Alvarez, the former Administrator of the U.S. Small Business Administration, into re-delegating her 8(a) contract signature authority to all Contracting Officers at the U.S. Agency for International Development (USAID).
2. In so doing Ms. Alvarez apparently delegated her SBA 8(a) liquidation powers in violation of Delegatus Non Potest Delegare – one to whom power is delegated cannot himself further delegate that power – and so all 8(a) contracts signed by USAID officers since May 1998 are void.
3. In 1998, Serco became the mentor operator of an 8(a) Base One Technologies server in Hillary Clinton's Chappaqua home and allegedly transmitted trigger signals to USAID for the liquidation bombings of the U.S. East African embassies on August 7, 1998.
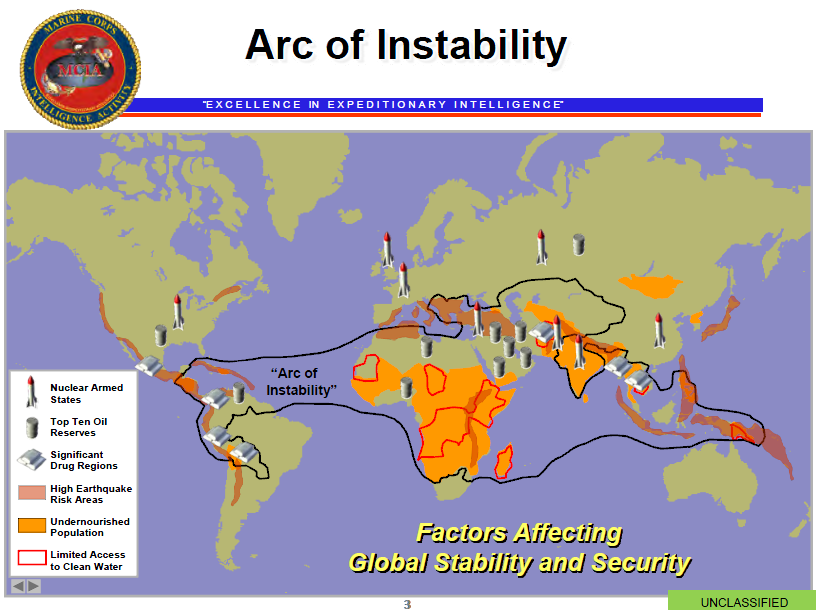
Field McConnell is standing by to brief Marine Corps General Joseph Dunford before requesting from Congress an authority by way of Letters of Marque and Reprisal to confiscate any servers operated by Serco for what the Marine Corps Intelligence Activity (oxymoron?) describes as the "Arc of Instability" under powers illegally delegated in the 8(a) USAID agreement of May 1998.
An alleged 8(a) USAID agent hired through Serco's National Visa Center in 1994 and provided with a Base One Technologies document conversion service prior to his presidential election campaign of 2008
United States Marine Corps security guard Jesse Nathanael "Nathan" Aliganga, murdered in the 1998 U.S. embassy bombings in Nairobi, Kenya.
Extorted former boss of Field McConnell’s sister Kristine Marcy during embassy bombings.
Serco's source of synchronized trigger signals for 8(a) USAID's Embassy, 9/11 and 7/7 bombings.
Prequel 1: #2409: Clinton's USAID Snuff-Betting Emails – Serco's Ultra Vires 8(a) Time Stamps – Marine Corps Navy Clock
"The 1998 United States embassy bombings were a series of attacks that occurred on 7 August 1998, in which hundreds of people were killed in simultaneous truck bomb explosions at the embassies of the United States in two East African cities – the Embassy in Dar es Salaam, the largest city of Tanzania, and the Embassy in Nairobi, the capital and largest city of Kenya.[1]
The attacks, which were linked to local members of the Egyptian Islamic Jihad, brought Osama bin Laden and Ayman al-Zawahiri—and their terrorist organization al-Qaeda—to the attention of the American public for the first time, and resulted in the Federal Bureau of Investigation (FBI) placing bin Laden on its ten most-wanted fugitives list. The FBI also connected the attack to Azerbaijan, as 60 calls were placed via satellite phone by bin Laden to associates in the country's capital Baku.[2] Fazul Abdullah Mohammed andAbdullah Ahmed Abdullah were credited for being the masterminds behind the bombings.[3][4][5]"
"Jesse Nathanael "Nathan" Aliganga (October 17, 1976 – August 7, 1998) was a United States Marine Corps security guard who was killed in the 1998 U.S. embassy bombings in Nairobi, Kenya. He was the only U.S. Marine killed in the bombings.
Aligana was working at the American embassy in Nairobi, Kenya. On August 7, 1998, at the age of 21, Aliganga was killed by a car-bomb explosion, along with eleven fellow Americans, in the suicide bomb attack. Aliganga was the only U.S. Marine who was killed in the attack in Kenya. This was part of a simultaneous suicide bomb attack in which car bombs were exploded at U.S. embassies in Tanzania and Kenya, killing 257 people and wounding over 4,000. The attack was later determined to be conducted by the al-Qaedanetwork and Osama bin Laden."
“In constitutional and administrative law, the principle delegata potestas non potest delegari (Latin) states that "no delegated powers can be further delegated". Alternatively, it can be stated delegatus non potest delegare, "one to whom power is delegated cannot himself further delegate that power".[1] This principle is present in several jurisdictions such as that of the United States, the United Kingdom and India"
“CONTRACT INFORMATION BULLETIN 98 - 15 The Small Business Administration (SBA) has launched a new pilot program to delegate 8(a) contract signature authority to individual agencies. This program is effective for one year, until terminated or extended, beginning in May of 1998. The SBA has delegated its authority under Section 8(a)(1)(A) of the Small Business Act (15 USC 637(a) as amended) to USAID to enter into 8(a) prime contracts, and its authority under Section 8(a)(1)(B) of the Act to subcontract the performance of that contract to an eligible 8(a) Program Participant. I hereby re-delegate said 8(a) contracting authority to all Contracting Officers at USAID. This delegation shall be in effect until the authority from the SBA is withdrawn. USAID has signed a Memorandum of Understanding (MOU) with the SBA that will eliminate the tripartite agreement and allow us to execute a single contract document to serve as the legal instrument between USAID and the 8(a) contractor. The MOU, which is attached to this CIB, explains the new award procedures and the responsibilities of the parties. Of the USAID responsibilities, the Office of Small and Disadvantaged Business Utilization(OSDBU), not the Office of Procurement, shall: 1. submit summary reports of all 8(a) contracting activities, as required by the MOU, to the SBA's Assistant Administrator for Business Development, Office of Minority Business Enterprise, on a quarterly basis; and 2. ensure that all applicable requirements of 13 CFR 124 are followed. The SBA has obtained a class deviation from the 8(a) award procedures contained in Federal Acquisition Regulation (FAR)19.8, which will be sent to all Contracting Officers and negotiators when it is received by the Agency. The MOU may be amended at any time by mutual agreement between the SBA's Associate Administrator for Minority Enterprise Development (AA/MED) and USAID's Procurement Executive. All amendments will be in writing. The MOU may be terminated by either the SBA's AA/MED or USAID's Procurement Executive upon thirty (30) days advance written notice. If the test program is successful, the MOU and all delegations of authority may be extended. I have also signed a class deviation to FAR subparts 19.8 and 52.2 (attached) to implement model language that will be incorporated in the FAR following promulgation of an SBA final rule. Use the model language attached to the deviation for your 8(a) contracting actions. Attachments 1) Memorandum of Understanding between USAID and SBA 2) Class Deviation w/attachment MEMORANDUM OF UNDERSTANDING between the U.S. SMALL BUSINESS ADMINISTRATION and the U.S. Agency for International Development I. PURPOSE The purpose of this Memorandum of Understanding (MOU) between the U.S. Small Business Administration (SBA) and the U.S. Agency for International Development (USAID) is to establish streamlined procedures for the award of requirements pursuant to Section 8(a) of the Small Business Act (15 USC 637(a)as amended), hereinafter referred to as "the Act." II. OBJECTIVES a. To reduce the interval between the time USAID sends offering letter to SBA and SBA's acceptance of the offering to a maximum of five (5) working days. b. To eliminate SBA approval of contracts executed under the authority of this MOU. c. To establish a uniform policy and procedure regarding the application of Simplified Acquisition Procedures (SAP) to the 8(a) contracting process, when applicable. ….
XI. ACCEPTANCE The undersigned parties hereby accept the terms of this MOU:
J. Brian Atwood, Administrator U.S. Agency for International Development Marcus L. Stevenson , Procurement Executive, U.S. Agency for International Development Ivan Ashley, Director Office of Small and Disadvantaged, Business Utilization/Minority Resource Center, U.S. Agency for International Development Aida Alvarez, [The allegedly extorted] Administrator U.S. Small Business Administration William A. Fisher Acting Administrator for Minority Enterprise Development, U.S. Small Business Administration Richard L. Hayes. Associate Deputy, Administrator for Government Contracting and Minority Enterprise Development, U.S. Small Business Administration http://www.usaid.gov/sites/default/files/documents/1868/cib9815.pdf"
"Hillary's Power Grab
The secretary of State has wrested control of USAID and influence over billions in foreign assistance. Tara McKelvey talks to the organization’s new head—dubbed her "minion," by one—about their agenda.
The Foggy Bottom Smackdown, as it is known in Washington, quietly unfolded in recent weeks. Round One went to Secretary of State Hillary Clinton for taking away power that administrators of a rival agency, the U.S. Agency for International Development, had managed to hold onto during the Bush administration. Even worse, Rajiv Shah, the new head of USAID, is a Hillary “minion,” as one insider puts it, who has hardly put up a fight.
One year after the Haiti earthquake, Clinton and Shah are shining a spotlight on the disaster. The Washington fight over foreign assistance may seem arcane in contrast to the magnitude of the tragedy—focusing on flow charts and budget lines—but it affects millions of people around the world. Luckily, some specialists, both inside and outside of government, are pushing for more autonomy for the development agency.
They should fight harder, because "the evisceration of USAID," as one development expert calls it, has serious consequences. Despite the rhetoric of administration officials, development work is being transformed from a mechanism that pulls people out of poverty into a tool of military intervention. That is Hillary's goal, and she should be stopped.
When aid money is managed wisely, people who live in the Democratic Republic of Congo and in other marginalized countries directly benefit. When funds are managed poorly, the money goes to less-deserving regions or is squandered on bad projects, often in countries where American troops are located. Not that USAID's Shah is complaining. He joined the administration as an undersecretary of Agriculture in 2009 and soon traveled with Clinton to Kenya, helping to write a speech that she gave that fall in New York.
When asked if development work has been too closely aligned with national security, Rajiv Shah lets out a heavy sigh. "A meaningless debate," he says. "We are trying to achieve development results that keep our country safe."
Several weeks later, he got a phone call: "Hi, Rajiv. This is Hillary.'" Sitting in his sixth-floor office in USAID headquarters at the Reagan Building, he shakes his head and laughs. "Doesn't happen every day," he says. She asked if he wanted to run the agency, and he started last January.
The 37-year-old native of West Bloomfield, Michigan, is hardly a "titan," as one aid expert points out, though he has a background in development. He worked in South India for four months on a tuberculosis project in the mid-1990s and, as he recalls, "I felt that was something I wanted to commit myself to." After medical school he joined the Bill and Melinda Gates Foundation in 2001. At USAID, he speaks of applying a business model: "We are trying to make our work as results-oriented as possible."
At nine on a weekday morning, he was dressed in a crisp shirt, shiny black shoes and neatly pressed trousers, though he had arrived home from El Salvador at two that morning. (As the father of three, including a 2-1/2-month-old baby, he is used to sleepless nights.) He looked annoyed when I mentioned that some aid specialists want his position raised to a Cabinet level and that “you’d have a bigger office."
"This is plenty large for me," Shah says, looking around the room. He has a point: The palatial corner office has a wooden desk, a 10-person conference table, a couch, and seven other chairs scattered about. When asked if development work has been too closely aligned with national security, he lets out a heavy sigh. "A meaningless debate,” he says. "We are trying to achieve development results that keep our country safe."
While he is dismissive of the conflict between USAID and the State Department, it has philosophical underpinnings: In the mid-1980s, as Carnegie Endowment Vice President Thomas Carothers recalls, the two agencies were housed in the same building, yet each had different Zip codes; the discrepancy was reflected in the mindset of staffers. "People in USAID thought they were fighting poverty and trying to do good, and State was serving national interests," says Carothers, who worked for the State Department. "You'd go to the other floor and think, 'Wow. This is a different world.'"
Not surprisingly, many State Department staffers look down on the do-gooders. "We used to laugh about it," says a senior-level official who had previously worked on national-security issues for the Bush administration. "We'd hear USAID people saying, 'We're an independent organization reporting to the secretary of State,' and we'd say, 'Oh-k-a-a-a-a-y.'" For these State Department officials, Hillary Clinton, who had served on the Senate Armed Services Committee, was a godsend. "When Clinton was nominated to secretary, those of us opposed to a Department of Development said, 'Game over.'"
Indeed, Hillary Clinton's approach holds sway. As Carnegie's Carothers points out, most assistance goes to a handful of countries, such as Afghanistan, Iraq, and Pakistan, that are strategically important to the Pentagon. For the 2011 fiscal year, the top two recipients of USAID and State Department assistance are Afghanistan, with a request for $3.92 billion, and Pakistan, with a request for $3.05 billion, while two of the poorest countries in the world are slated at only a fraction of that amount: Democratic Republic of Congo ($213 million) and Niger ($18.5 million).
People who live in Congo and Niger may suffer from civil war and famine, but there is little to be gained from helping them, while "over in Country B they have nuclear weapons," says Carothers. Yet not everyone takes a realpolitik approach to development work; in Britain, according to The Economist, 90 percent of foreign assistance is supposed to go to the world’s most impoverished countries.
Still, Clinton and her acolytes have a point. Last month, Rep. Ileana Ros-Lehtinen, a Florida Republican who now chairs the House Foreign Affairs Committee, announced that she planned to cut foreign aid because "there is much fat." With the federal budget under enormous pressure, it is easier to convince lawmakers to fund development programs when they are linked to strategic interests.
Yet development programs that are thrown together quickly, and designed for military and strategic goals, are likely to fail—or even worse, will lead to "perverse results," as one specialist says, since experts generally work with local groups for years until the projects take root. (Like most people interviewed for this article, he asked not to be identified.)
Developing the infrastructure of a devastated country like Afghanistan takes time, and flooding the zone with money makes things worse. The main beneficiaries of U.S. foreign assistance have been the tribal leaders who became business partners with American contractors and friendly with U.S. officials, and the losers are ordinary Afghans who are left out of the deals. "The overriding criticism of aid efforts was the perception of massive corruption that is both fueled by, and undermines the impact of, aid programs," wrote development specialist Andrew Wilder in a December 2009 essay, describing tribal leaders in Urozgan province who "not only got all the power in government," as one Afghan official explained, "but also controlled and benefited from all the aid programs."
For these reasons, some people in Washington are quietly encouraging Shah to strengthen the agency so that foreign assistance can be managed in a more rational way, allocating additional resources to countries in need, such as Congo and Niger, and not overwhelming countries like Afghanistan with dollars and corruption scams. Clinton's December report on foreign policy, known as the Quadrennial Diplomacy and Development Review, granted Shah authority over initiatives, such as an agricultural program called Feed the Future, for example, yet the report also ensured his budget would remain under the State Department. Overall, USAID lost ground. "There's no fighting against Hillary Clinton in this environment," says Brookings' Noam Unger, who studies the U.S. policies of foreign assistance. "It doesn’t happen."
Development work directly linked to strategic interests shows a dodgy rate of success, and there is another question: Is this the kind of country Americans want? The U.S. recently pulled out of one disastrous war and is currently enmeshed in another, and altruism has benefits: Helping people because it is the right thing to do, not because it serves our interests, might make us feel a little less crummy about ourselves.
Tara McKelvey, a frequent contributor to The New York Times Book Review, is the author of Monstering: Inside America's Policy of Secret Interrogations and Torture in the Terror War (Basic Books)."
"Hillary Clinton's Custom Email Based on Server Near Her Home
Setup raises questions of security and transparency
…
Paul Vixie, who founded a Bay Area cybersecurity firm, Farsight Security, said that if Mrs. Clinton hired someone with the appropriate level of skill to set up her server, it would have been more secure than using a government email account.
"Nothing is completely wizard-proof, but if you do a good job you can raise the costs of any attacker to a point where it's probably not worth their while to break in," he said.
Some experts were more skeptical of Mrs. Clinton's choice.
With a private email server, "she's on her own," said Christopher Soghoian, a technologist at the American Civil Liberties Union. "We don't know if she herself was running her email server or if she had someone she was paying to do it. But we would imagine they don't have the skill and resources the State Department and [National Security Agency] do."
The government has faced its own challenges in securing email accounts. Last month, The Wall Street Journal reported that after three months of trying, the State Department had yet to expunge hackers linked to Russia from its unclassified email system.
The Internet connection that Mrs. Clinton's computer server used was registered to a man named Eric Hoteham, whom the Journal and the AP couldn't locate. The name is similar, however, to that of Eric Hothem, a longtime Clinton aide who currently works at J.P. Morgan Chase & Co. [Serco shareholder] in Washington, D.C. Mr. Hothem couldn't be reached for comment Wednesday.
Other domains linked to the clintonemail.com network include mail.president.clinton.com, printer.presidentclinton.com and wjcoffice.com. Former President Bill Clinton's full initials are WJC."
"Serco's Office of Partner Relations (OPR) helps facilitate our aggressive small business utilization and growth strategies. Through the OPR, Serco mentors four local small businesses under formal Mentor Protégé Agreements: Three sponsored by DHS (Base One Technologies, TSymmetry, Inc., and HeiTech Services, Inc.,) and the fourth sponsored by GSA (DKW Communications, Inc.). Serco and HeiTech Services were awarded the 2007 DHS Mentor Protégé Team Award for exceeding our mentoring goals." http://www.dtic.mil/whs/directives/corres/pdf/100515p.pdf
"Base One Technologies – Corporate Strategy – We are a Government Certified Women-Owned Business
We practice Diversity Recruitment and Staffing for IT positions
Base One was founded in 1994 by a women engineer who had made a career in technology research for many years. Base One has been very successful in focusing on diversity recruiting and staffing for IT projects. It has been our experience that the greater the diversity mix, the more creative the solution. As in any field the more diverse the viewpoint the more thorough your analysis. Our engineers can think out of the box.
Because of our affiliations we have access to pools of resources among more diverse groups & individuals. We work with a large pool of minority professionals who specialize in IT skills. We are able to have access to these resources through our status as a D/MWBD firm and our affiliations. These affiliations assist us in working with resources among more diverse groups & individuals.
We are also partnered with firms that are 8A certified as Minority firms, Disabled Veteran firms, Native American firms, Vietnam veteran firms, women owned firms.
Our hub zone location keeps us close to the professional organizations of great diversity. We are active in recruiting from and networking with these community organizations of local IT professionals. This has given us access to a large pool of diversity talent.
Base One's staff of engineers are a diverse group of professionals. This diverse network of engineers helps us to branch out to other engineers and creates an even larger network of resources for us to work with.
The greater the diversity the more complete & thorough the analysis. The broader the spectrum of points of view the broader the scope of the analysis. We feel that a diverse team gives us a greater advantage in creating cutting edge solutions. To that end we will continue to nurture these relationships to further extend our talent pool.
The greater the diversity mix, the more creative the solution.
The more diverse the viewpoint, the more thorough the analysis.
The more diverse our team, the more our engineers can think out of the box.
This is why Base One Technologies concentrates on diversity recruitment in the belief that a diverse team gives us a greater advantage in creating cutting edge solutions."
Information Security Planning is the process whereby an organization seeks to protect its operations and assets from data theft or computer hackers that seek to obtain unauthorized information or sabotage business operations.
Key Clients Benefiting From Our Information Security Expertise: Pentagon Renovation Program, FAA, Citigroup, MCI.
Base One technologies
Expertly researches, designs, and develops information security policies that protect your data and manage your firm's information technology risk at levels acceptable to your business.
Performs architectural assessments and conducts both internal and external penetration testing. The results of these efforts culminate in an extensive risk analysis and vulnerabilities report.
Develops, implements and supports Information Security Counter measures such as honey-pots and evidence logging and incident documentation processes and solutions."
"Pando – The murderous history of USAID, the US Government agency behind Cuba's fake Twitter clone
"In a number of countries, including Venezuela and Bolivia, USAID is acting more as an agency involved in covert action, like the CIA, than as an aid or development agency."
—Mark Weisbrot, Center for Economic and Policy Research Last week, we learned from the Associated Press that USAID (United States Agency for International Development) — the government agency which manages billions in overseas "humanitarian" aid programs — plotted to overthrow Cuba's communist regime via a covertly-funded fake Twitter platform.
The idea was to get Cuba's youth to sign up for ZunZuneo (Cuban slang for the sound hummingbirds make—get it?) without anyone knowing about USAID's involvement, get the kids hooked on pointless tweeting, collect all sorts of data on the users, and then rile them into an anti-regime rage — a "Cuban Spring" revolution.
Presumably the US government had been studying Twitter's ability to supercharge its users with outrage vapors here in the Free World, where legions of credulous idiots spend their waking hours chasing the outrage dragon. It was only a matter of time before some DC spooks and Northern Virginia contractors would see the angles.
Of course, the ZunZuneo plan failed. ZunZuneo collapsed, a bunch of money went missing (likely into the coffers of the Castro regime's state-controlled telecoms firm, or so they say), and the Communist Cuban menace still threatens the Free World’s slick underbelly.
What really seems to be weirding people out here is the shock realization that USAID — the nice, humanitarian, democracy-promoting arm of American idealism — also engages in sleazy regime-change and subversion. The sorts of nefarious covert activities folks normally associate with the CIA.
Not that this is news to PandoDaily readers, of course: Earlier this year, we broke the story about USAID co-investing with Omidyar Network in Ukraine NGOs that organized and led the Maidan revolution in Kiev, resulting in the overthrow of President Viktor Yanukovych. That revolution hasn't turned out so well — thanks to the "success" of the USAID-Omidyar-funded revolution, there's talk of the West going to war with nuclear-armed Russia, Ukraine is losing entire chunks of territory like the proverbial leper on a waterslide, Kiev is run by a coalition of costume-party fascists and a handful ofbillionaire Mafia dons—and Vladimir Putin has never been more popular, or more tyrannical.
Given USAID's "success" in Ukraine, perhaps we should be thankful that ZunZuneo failed as miserably and comically as it did.
For me, there wasn't anything all that surprising about the recent USAID revelations. I spent over a decade in Russia and the former Soviet Union, and witnessed for myself the good, bad and ugly that USAID funded—mostly the bad and the ugly. I assumed that most reporters already understood what USAID gets up to overseas, often alongside private nonprofits like those run by Soros, Gates, Rockefeller, Ford and more recently, Omidyar.
The truth is, USAID's role in a covert ops and subversion should be common knowledge—it’s not like the record is that hard to find. Either USAID has developed those Men In Black memory-zappers, or else—maybe we don't want to remember.
This selective amnesia doesn't do anyone else any good however, so I figured it might be useful to offer a brief look back at some of USAID's darkest, ugliest moments. It's important to note that not everything USAID does is patently evil — in fact, there are many programs that could even be described as good. But USAID, as with any agency of American power, is fully capable of and will continue to be an instrument of geopolitical and corporate force.
As Big Tech becomes increasingly intertwined with USAID's missions around the world — particularly as USAID's programs and language merge with thelexicon and interests of Silicon Valley (such as "Global Development Lab,"USAID's new "DARPA-like" research arm) — now's a good time to refresh our memories about USAID's dark past."
"The 8(a) Business Development Program assists in the development of small businesses owned and operated by individuals who are socially and economically disadvantaged, such as women and minorities. The following ethnic groups are classified as eligible: Black Americans; Hispanic Americans; Native Americans (American Indians, Eskimos, Aleuts, or Native Hawaiians); Asian Pacific Americans (persons with origins from Burma, Thailand, Malaysia, Indonesia, Singapore, Brunei, Japan, China (including Hong Kong), Taiwan, Laos, Cambodia (Kampuchea), Vietnam, Korea, The Philippines, U.S. Trust Territory of the Pacific Islands (Republic of Palau), Republic of the Marshall Islands, Federated States of Micronesia, the Commonwealth of the Northern Mariana Islands, Guam, Samoa, Macao, Fiji, Tonga, Kiribati, Tuvalu, or Nauru); Subcontinent Asian Americans (persons with origins from India, Pakistan, Bangladesh, Sri Lanka, Bhutan, the Maldives Islands or Nepal). In 2011, the SBA, along with the FBI and the IRS, uncovered a massive scheme to defraud this program. Civilian employees of the U.S. Army Corps of Engineers, working in concert with an employee of Alaska Native Corporation Eyak Technology LLC allegedly submitted fraudulent bills to the program, totaling over 20 million dollars, and kept the money for their own use.[26] It also alleged that the group planned to steer a further 780 million dollars towards their favored contractor.[27]"
"Loan Improvement Jan 31, 2001 SBA modernizes to help feed its growing programs
BY PATRICIA DAUKANTAS | GCN STAFF
Under a five-year plan for overhauling its information technology systems, the Small Business Administration recently acquired new software for financial and other administrative tasks. .. In the first phase of the modernization, the agency has upgraded systems for managing its extensive portfolio of guaranteed loans, chief operating officer Kristine Marcy [Field McConnell's sister] said. SBA processed its first electronic loan last November through its Sacramento, Calif., office and plans to add more private lenders during fiscal 2001. .. Marcy said. Banks had been asking SBA to make faster decisions on loan guarantees. The agency decided to aim for a [onion router] turnaround time of one hour. In the second phase of modernization, SBA is revamping its financial, human resources, procurement and travel systems with Web-enabled Oracle Corp. applications. .. The second-phase integrator, SRA International Inc. of Arlington, Va., has subcontracted with a number of small firms for things such as training and data conversion [Note Serco protégé Base One opened a document conversion center in the Bronx in 2006, presumably to deal with Obama's passport problems]. .. In the final phase of the modernization, SBA will upgrade the computers in its 8(a) Business Development Program, which assists small businesses in competing for government contracts, Marcy said. The agency wants to be able to improve its tracking of clients' successes and failures [through to liquidation by the SBA's preferred lenders and sureties such as HSBC and Travelers Casualty and Surety Company of America - note merged with Citigroup and John Deutch's CIA friends!]."
"On October 6, 2000, the NMCI contract was awarded to Electronic Data Systems (EDS), now HP Enterprise Services (HP).[11] Secretary of the Navy Gordon England summed up the Navy's IT Environment prior to the commencement of NMCI: "We basically had 28 separate commands budgeting, developing, licensing, and operating IT autonomously. It was inefficient and from the larger Department perspective, produced results that were far from optimal."[12]
NMCI consolidated roughly 6,000 networks—some of which could not e-mail, let alone collaborate with each other—into a single integrated and secure IT environment. HP updated more than 100,000 desktop and laptop PCs in 2007.[13] The program also consolidated an ad hoc network of more than 8,000 applications to 500 in four years and 15,003 logistics and readiness systems to 2,759 over a two-year period.[14]
Sub-contractors to HP include:
Apple Inc., Cisco, Dell, McAfee, Microsoft, Oracle Corporation, Sun Microsystems, and Symantec[15]
Harris Corporation (which acquired Multimax formerly known as Netco Government Services and WAM!NET), which provided enterprise network infrastructure design and support until its contract expired in 2014.[16]
Verizon, which provides wide area network (WAN) connectivity.
HP also provides the security services once provided by Raytheon.
"HP also has worked with more than 400 small businesses, with 5 percent for small disadvantaged businesses, 5 percent for women-owned small businesses and 1.5 percent for HUBZone small businesses. Since its inception, NMCI has exceeded the minimum 40% small business objective set for the contract.[17]
…
The Department of the Navy has shown no desire to scale back or cancel the program. On 24 March 2006 the Navy exercised its three-year, $3 billion option to extend the contract through September 2010.[1] In April 2006, users began to log on with Common Access Cards (CACs), a smartcard-based logon system called the Cryptographic Log On (CLO). In October 2008, NMCI’s prime contractor HP posted a set of procedures so Apple Mac users can access NMCI's public-facing Web services, such as the e-mail and calendar functions, using their CAC readers with their Macs. The workaround also works with other Defense Department CAC-enabled networks.[27] Alternatively, NMCI and all other CAC-authenicated DoD websites may be accessed using LPS-Public."
Thursday 25 June 2015 00.01 BST
The Ministry of Justice is still paying security firms G4S and Serco millions of pounds every month for supplying electronic tagging equipment, more than a year after both companies were barred from running the contract.
Both companies faced criminal investigations by the Serious Fraud Office over allegations of overcharging that led to them repaying nearly £180m.
The continuing monthly payments to the two companies were uncovered by an analysis of Ministry of Justice (MoJ) data by the Centre for Crime and Justice Studies which shows that G4S was paid a total of £8.7m between March 2014 – when it lost the tagging contract – and February 2015. Serco was paid £4.5m over the same period.
The electronic monitoring tags are used to enforce curfews on more than 100,000 offenders each year. The outsourcing giant Capita took over the contract on an interim basis in April last year.
In July 2014, Capita and three other companies were named as the winners of a £265m six-year contract to supply the next generation of satellite tracking tags, which would allow dangerous and repeat offenders to be monitored around the clock."
Serco... Would you like to know more?
SWISSLEAKS - "HSBC developed dangerous clients: arms merchants, drug dealers, terrorism financers"
Copy of SERCO GROUP PLC: List of Subsidiaries AND Shareholders! (Mobile Playback Version) [HSBC is Serco's drug-hub Silk Road banker and a major shareholder with the 9/11 8(a) lenders including Her Majesty's Government and JPMorgan]
Yours sincerely,
Field McConnell, United States Naval Academy, 1971; Forensic Economist; 30 year airline and 22 year military pilot; 23,000 hours of safety; Tel: 715 307 8222
David Hawkins Tel: 604 542-0891 Forensic Economist; former leader of oil-well blow-out teams; now sponsors Grand Juries in CSI Crime and Safety Investigation




No comments:
Post a Comment
Note: Only a member of this blog may post a comment.